
Mar 23, 2022
2 Comment by ViewersAs cloud innovation grows, so does the matter of security – whether there are adequate cloud security measures executed to avoid catastrophe. This is more real while dealing with the reliably changing landscape of innovation arrangements. Cloud-based arrangements have acquired various advancements in the industry. However, a disaster, for example, the Apple iCloud leak back in 2014 can indicate, data inside the cloud can be leaked because of cloud security. Thankfully the framework has created all through the years with various cloud security enhancements.
As cloud innovation grows, so does the matter of security – whether there are adequate cloud security measures executed to avoid catastrophe. This is more real while dealing with the reliably changing landscape of innovation arrangements. Cloud-based arrangements have acquired various advancements in the industry. However, a disaster, for example, the Apple iCloud leak back in 2014 can indicate, data inside the cloud can be leaked because of cloud security. Thankfully the framework has created all through the years with various cloud security enhancements.
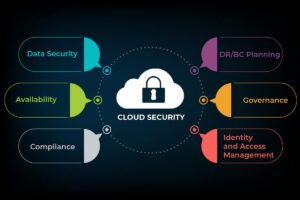
Cloud is as of now not a popular articulation of the past. In today’s reality, cloud innovation is being executed across several organizations. Whether it is a customer application, business data storage, or software advancement cloud figuring is being used across several industry verticals. Cloud enlisting is generally used for data storage capabilities. However, there is another thing to cloud figuring.
Cloud figuring enhances clients’ enlisting capabilities, meaning clients are not bound to the restricted assets of their physical PC. Cloud figuring has carried scalability and adaptability to enlisting. The necessity for executing complex frameworks has been taken out of the equation, rather cloud arrangements made operations and advancement easier for clients. And this way of operations has hugely helped one industry in the particular-the pharmaceutical industry.
As cloud innovation is being executed across various ventures, the requirement for cloud-based arrangements can be seen greatly in the pharmaceutical industry. The pharmaceutical industry deals with vast amounts of complicated data. Cloud services like Software as a Service (SaaS) are the bread and margarine of the industry.
In this case, the cloud holds pharmaceutical-explicit software and data for the undertakings operating in the industry. The software being utilized by pharmaceutical endeavors gathers crucial data and also has to process and move them in mass. And cloud figuring streamlines the entire cycle for companies. Hence, cloud security is an important worry in the pharmaceutical industry.
One reason why cloud security for this industry has such large importance is the US and EU regulations. In December 2018, the FDA gave a Q&A Guidance Document for the industry on “Data Integrity and Compliance With Drug CGMP” as a reaction to various data integrity violations during CGMP (Current Good Manufacturing Practice) assessments. And a clearer reason for cloud security for the pharmaceutical industry is simply the nature of the data.
The perplexing and various data a pharmaceutical venture deals with is regularly crucial to operations, as R&D. Thus, assuming the data gets leaked through malfunction or corporate espionage, the company will face massive misfortunes and setbacks. In this way, cloud security is a key factor while executing cloud-based advances in the pharmaceutical industry.
With all that said, we as a whole realize that cloud innovation will just develop pushing ahead maybe even become old by the following technological interruption later on. According to Gartner, most undertakings are centered around mitigating digital dangers in the forthcoming years, to make sure none of their valuable data falls into some unacceptable hands.
However, as cloud registering develops, so mists security-as the security conventions need to keep up and counter any escape clauses that can be exploited. After some broad research on how we maintain our cloud security and many other professional sources-here are the key patterns I accept we will be seeing for cloud security later on.
Incorporation of AI/ML As artificial intelligence is being executed in all technological innovations, turning into a central participant in industry 4.0. An article from The New Stack predicts that machine learning would become integral in maintaining cloud security throughout the next few years. Machine Learning can identify and learn client behaviors and information in this manner creating and changing security conventions for the clients to keep interlopers at bay.
Manage Vulnerability With cloud figuring advancing at a rapid pace, it has turned into a necessity to train clients on the importance and approaches to maintain cloud security. Cloud figuring has advanced to the point that it is almost difficult to blame any mishap on cloud service suppliers. ZYMR called attention to that cloud service suppliers update their security infrastructure regularly.
The came about security botches usually come as remote work logging, insider threats, misconfigured frameworks, disseminated denial of service, IT and OT combination, split the difference in credentials, lacking the expected level of investment, uncertain APIs, crypto-jacking, weak security measures, IoT gadgets, or containers, or any other phenomenal factor.
This leads to the ascent of many security microservices and containers later on. The utilization of containerized apps has made it easy for clients to manage and chip away at the cloud-as such any weak connections are expected to be practiced with legitimate audit and action.
Cloud Related Regulations and Compliance I recently called attention to that to work in the pharmaceutical industry, software companies should adhere to regulations by Q&A rules of the FDA and CGMP practices. What holds in what’s to come are more rigid and industry-centered laws for cloud figuring. In the present, there are many practices of cloud security through data encryption; and compliance regulation for banking and healthcare enterprises.
cloud security should be guaranteed while utilizing cloud figuring services. This sounds accurate for enterprises, for example, the pharmaceutical, where a great many valuable data are gathered, put away, and dealt with. With our broad work in the pharmaceutical industry, we at Pridesys IT LTD have secured the specialty of giving the best technological innovations in the industry.
And with any cloud processing services we cater to, cloud security is our most extreme priority and aims to convey the best service. Along these lines, contact us to be aware of our cloud processing services!